Back to Section 1 - What is a Social Engineering Attack?
 A real-world social engineering attack scenario could play out something like this:
A real-world social engineering attack scenario could play out something like this:
The attacker has deployed various exploits for common software and operating system vulnerabilities on a decoy website. He then sends an email message containing a link to the infected site, to potential victims in his target company. An employee clicks this link and, as soon as the webpage loads, every single malicious script installed on it will check that employee’s workstation for viable software to exploit. If any match is found, the workstation can be infected with malware. This, in turn, exposes the entire corporate network to infection.
The US Government’s National Vulnerability Database¹ keeps a running track of software vulnerabilities, as these emerge. At the time of writing (Aug 2, 2019), almost 10,000 new CVEs (Common Vulnerability Exposures) have emerged this year alone. Worse still, only slightly more than fifty percent of these have been patched by the affected software developers.
For example, in the above scenario, if the employee is running an out-of-date version of Microsoft Internet Explorer, the attacker is able to hijack the web browser and potentially the employee’s entire workstation, by exploiting CVE-2017-0037 ², which is just one of countless vulnerabilities listed in the National Vulnerability Database.
Worse still, criminals frequently bundle multiple attack vectors into a single intrusion attempt, to increase their chances of success. Therefore a phishing email might contain a link to an attack website, as well as an attachment packed with multiple malicious scripts. While the target’s antivirus software may catch the attached scripts, there is no defense against the victim visiting the attack website and entering his or her username and password for use by the attacker.
 To a cyber security professional it’s obvious why it’s a REALLY BAD IDEA to run an unknown attachment, click a dubious link, or enter your login credentials on a suspicious website. A great many employees, however, will perform the above actions without much hesitation when faced with a targeted social engineering or cyber attack. Statistics show that data breaches were up eleven percent in 2018, year-on-year³ and that between eleven and seventeen percent of employees will fall for phishing emails⁴.
To a cyber security professional it’s obvious why it’s a REALLY BAD IDEA to run an unknown attachment, click a dubious link, or enter your login credentials on a suspicious website. A great many employees, however, will perform the above actions without much hesitation when faced with a targeted social engineering or cyber attack. Statistics show that data breaches were up eleven percent in 2018, year-on-year³ and that between eleven and seventeen percent of employees will fall for phishing emails⁴.
A fascinating, yet terrifying study⁴, based on mock social engineering attacks against 3,300 corporate employees, established that between eleven and thirty-three percent of staff are susceptible to phishing and spear-phishing, depending on the attack vector and topic used by criminals.
The Employee types of those who did ”commit unsafe actions” as a result of a phishing or spear-phishing email are listed in the following graphic.
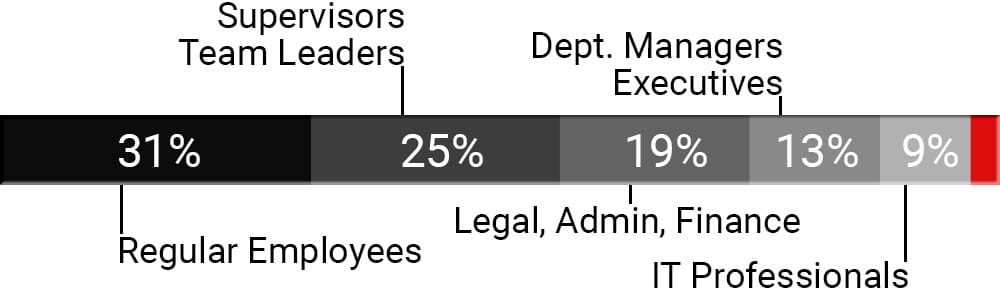
Most alarming of all is the fact that the last three percent (The Red Segment) on the graph is made up of Cyber Security Professionals, employed to prevent this type of attack in the first place.
You know the threat is terrifying if even some cyber security professionals fall victim to a targeted social engineering attack.
And that's not all... The same study also reveals that certain employees will actively respond to attack emails, most frequently with comments that the attachment failed to open. In extreme cases employees would even forward the email to their colleagues, with notes telling them to ”Open the Attachment”, thus adding a layer of internal legitimacy to a phishing attempt. Other respondents wrote back, stating “You have the wrong person. Try this other person.” and including the other person's contact details.
Once a member of staff responds to phishing email, the attacker can be sure that his/her victim is clueless they’re responding to a criminal. At that point the criminal will invariably make further contact with the victim, in an effort to either fulfill the attack’s purpose, or to gather intelligence (employee names & email addresses, company antivirus and software versions, cellphone numbers, etc.) to aid in the current intrusion attempt or in future attacks. Any information given away by the hapless staff member can carry grave consequences for the entire company.
In order for their phishing email to pass as legitimate, more sophisticated attackers resort to registering domain names which look similar to that of the target company. Misspellings make up the majority of fraudulent domain names registered. So a social engineering attacker looking to send “Windows 10 Support Email” might choose to register mircosoft.com⁵, because it passes the ”At a Glance” test when it lands in a victim’s inbox. Other means of subterfuge include expanded/departmentalized domain names (jpmchaseaccountsreceivable.com) or hyphenated domain names (jpm-chase-accounts-receivable.com), which mimic the look and feel of the criminal’s target company.
The simple fact is that few computer users outside the IT sectors pay much attention to the URLs on their screen and in their inboxes. So long as it looks about right, it passes. This is a huge factor in the scammers’ favor.
Criminals have learned to channel greed, fear, and doubt into making potential victims drop their guard and abandon their natural caution. Consequently, attack email subject lines have become more ”crafted” to draw a response, over time. When a user receives an email with the subject: ”Important message about lack of funds in your account.” from jpmchaseaccountsreceivable.com, it’s easy to throw caution to the wind, open the email reflexively, and visit the proffered link to ”set things straight”.

 In a corporate environment, subject lines such as ”Mail Delivery Failed: Annual Bonus Level Sheet” or ”Confidential: Staff Termination List” can provoke similar actions from curious or insecure employees.
In a corporate environment, subject lines such as ”Mail Delivery Failed: Annual Bonus Level Sheet” or ”Confidential: Staff Termination List” can provoke similar actions from curious or insecure employees.
WARNING: Criminals know that well crafted subject lines and lookalike domain names greatly increase opening and action rates. The more emotive the subject, the greater the likelihood of your staff forgetting security principles and acting on impulse.
HUMAN EMOTIONS... THE WEAKEST LINK
Findings⁴ indicate that almost forty percent of users who received a phishing email with a termination-based subject line ended up committing unsecure actions. Subject lines promising wage increases, rewards, or bonuses also drew high response rates, with almost twenty-five percent of recipients falling prey to the lure. It’s unsurprising that fear of dismissal or joy at a prospective pay rise cause a greater percentage of unsafe actions. Social Engineers are experts at manipulating human emotions.
It's not always an email. A bogus tech support call can also entrap victims. The past few years have seen a marked increase in phone-based social engineering attacks. Here’s one frequent scenario used against Microsoft Windows home users: Callers claiming to represent Microsoft's support department contact the potential victim about a “Security Vulnerability in the Windows Operating system”. If the victim responds positively, the caller will then instruct them to install a Virus Cleaning Application or grant him/her remote access, so ”the problem can be fixed” directly by ”Microsoft staff”. Before long, the victim has a computer chock-full of malware and the attacker has enough personal information to commit identity fraud, as well as access to all the victim’s bank accounts and credit card information.
This tactic is also effective against companies. At the corporate level, however, the scam works somewhat differently. Commonly the victim will receive a call at home, late at night or early on a weekend morning, ostensibly from his/her company's IT department, and be asked to head to the office as soon as possible due to a major problem. Shocked, the victim will ask questions and, as the conversation evolves, the IT support worker will ask for the victim’s login details, so the issue can be sorted without ”causing unnecessary inconvenience”.
A variation on this approach will see the attacker provide the victim with a support URL, to log into the system and check out the situation. When this URL fails to resolve, the criminal will then ask for the login credentials. In either scenario, the victim has just handed over access to the company network with a smile and a thank you.

 In this often overlooked scenario, the attacker will frequent a public food court, either in or near the target company office building. He/she will then surreptitiously ”shoulder surf” surrounding users who are working on laptops and tablets. Due to the unsecured environment, this technique allows criminals to gather a significant number of usernames and passwords through simple observation, without ever sending an email or contacting a single employee personally.
In this often overlooked scenario, the attacker will frequent a public food court, either in or near the target company office building. He/she will then surreptitiously ”shoulder surf” surrounding users who are working on laptops and tablets. Due to the unsecured environment, this technique allows criminals to gather a significant number of usernames and passwords through simple observation, without ever sending an email or contacting a single employee personally.
Another, more recent, variation of this technique sees the criminal actually creating ”Fake Public WIFI Zones” in places like the above food courts and other public spaces, and simply wait for the people around them to connect to their devices to his/her malicious honeypot. Once their devices are part of the fake network, it becomes a simple matter to collect usernames, passwords, and a number of other pieces of confidential data⁶.

 In the days before social media, gathering enough detailed intelligence about individuals to support a targeted social engineering attack was a prolonged process, requiring physical surveillance in many cases. For the most part, the same level of knowledge (or better) can now be gleaned from poring over the intended targets’ Facebook profiles.
In the days before social media, gathering enough detailed intelligence about individuals to support a targeted social engineering attack was a prolonged process, requiring physical surveillance in many cases. For the most part, the same level of knowledge (or better) can now be gleaned from poring over the intended targets’ Facebook profiles.
Further, most people are Facebook-connected with their colleagues. They also tend to ”Talk Shop” on social media and even share company information and/or documents with others, over this hideously poorly secured communication channel. Therefore, given half a day’s focused research, a determined attacker can easily build a fairly accurate picture of any given department’s staff and of their interpersonal relationships. This familiarity with departmental structure, the employees within it, and any corporate data gleaned can be used to devastating effect when combined with the social engineering attack vectors and scenarios outlined above.
Lastly, many businesses allow staff to sign into social media accounts from company hardware. This opens the door to a single malicious link, shared over Facebook, providing direct access into a company network.
As a rule, if your employees publicize their place of employment on Facebook, or any other social media website, they must be made fully aware of the associated vulnerabilities and of their responsibility to corporate cyber security, even when they’re not at work.
Phishing and Spear-Phishing continue to be the weapons of choice for attacks on corporate infrastructure. From a purely pragmatic standpoint, this is because the two tactics provide scammers with far and away “the most bang for their buck”. They are simple, cheap, and exceedingly effective, even against supposedly hard targets, simply because humans are ALWAYS the weakest link in any security chain. Just ask John Podesta⁷.
Next up: Section 3 - Defenses & Risk Reduction

Sources:

The number of cyber attack verctors is growing on a daily basis, with phishing, business email compromise, and social engineering at the head of the line. We safeguard your crucial systems against the growing number of threats facing them. Find out more...